
In the modern world of networks, the protection of our devices is a top priority. iPhones are prime examples of gadgets that need security against viruses. Although it might be unpleasant to consider that someone else could be able to access your device remotely, you can protect your privacy by taking appropriate measures and educating yourself. Basic remote access indicators, how to spot unusual activity, and important precautions to prevent possible hacking are all covered in this article. We are sure that by the end of this article, you will be able to assess whether someone is accessing your iPhone remotely.
Common Signs Showing Someone is Remotely Accessing Your iPhone
Identifying the signs of someone accessing your iPhone is the first step towards protecting it. Be aware of the following warning signs:
-
Unexplained Battery Drain:
– If your phone’s battery is draining quickly, this may indicate the presence of unauthorized apps.
-
Slow Performance:
– Any significant lags or slowdowns could be a sign of illegal usage of system resources and remote access.
-
Unexpected Data Consumption:
– An unusual boost in data consumption that breaks from the established pattern may be an accurate signal that some unauthorized person was remotely accessing your device.
Analyzing Unusual Activity of Remote Access
Monitoring is crucial for spotting potential remote access in terms of control. Follow these actions to spot indications of unwanted access:
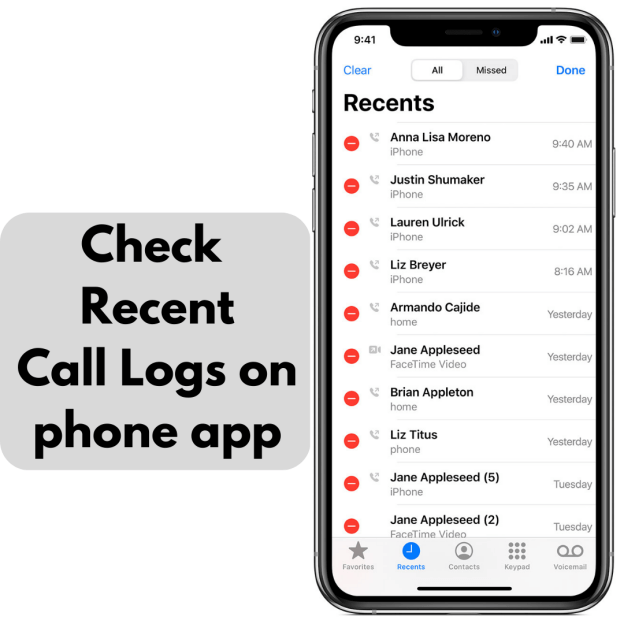
-
Analyse Recent Calls and texts:
– Make sure that any strange incoming or outgoing calls and texts are verified. Any calls or messages that were not made from your device should not go unnoticed in any situation since this is a major factor, which should be analyzed to make your device hackingproof.
-
Monitor App rights:
– Examine the rights granted to installed apps, paying particular attention to any inactive or doubtful ones.
-
Check Recently Installed applications:
-Be careful to go through any newly installed applications that weren’t installed with your knowledge or approval.
Tracking Battery Usage and Performance
Keeping an open eye on battery usage and performance might provide important information about any remote access attempts. If someone tries or keeps trying to gain access to your iPhone, then the following are the things that should be checked on the first instance:
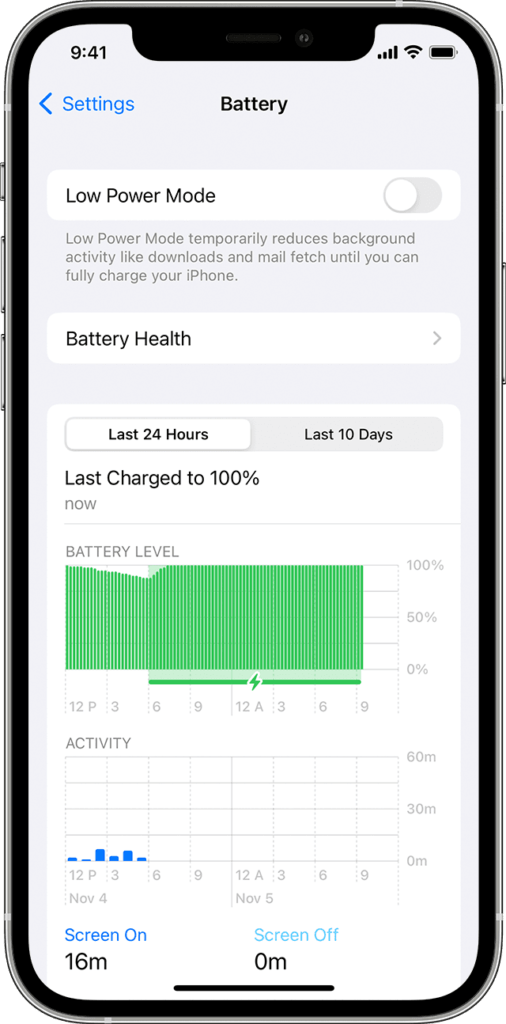
-
Check Battery Usage:
– You may check the settings of your iPhone to see which applications use the most battery. Unknown applications with high power consumption may indicate fraud.
-
Check for System Performance Problems:
– Take note of any irregular pauses, crashes, or inactivity; these might be the result of an attempt at remote access.
-
Make Use of Performance Analysis Apps:
-To get more detailed information on how your iPhone operates, you may try utilizing performance monitoring apps that are provided by third parties.
Detecting Suspicious Network Activity
Network connections are typically a part of remote access. Keeping an eye on the network traffic on your iPhone allows you to spot suspicious activity:
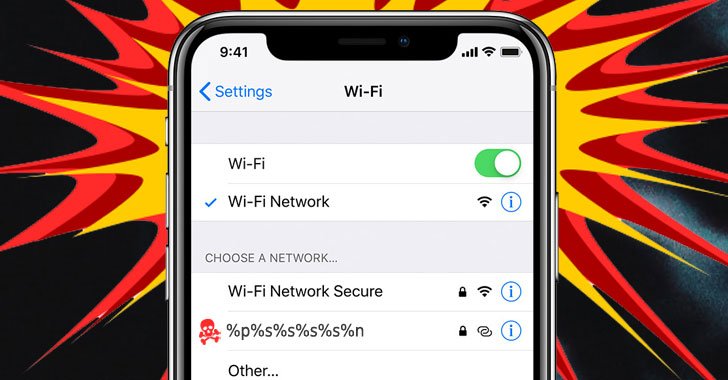
-
Analyse Active Connections:
– Go to Settings > Wireless or Settings > Wi-Fi and check the list of active connections, making sure to include any unknown devices.
-
Monitor Data Transfers:
– Monitor data moving processes, particularly if you do not use a data-intensive application or service.
Examining Unfamiliar Apps and Settings
Identifying potential remote access requires a close examination of the apps and settings on your iPhone:

-
Review Installed Apps:
– Scrutinize and discard any unrecognizable or doubtful apps that you are not sure to have installed on your phone regularly.
-
Scrutinize System Settings:
– Inquire about any changes in the settings of your iPhone, for instance, alterations in security options or activation of unknown sources for app installation.
Analyzing Battery Drain and Data Usage Patterns
Patterns in battery drain and data usage can provide valuable insights into potential remote access:
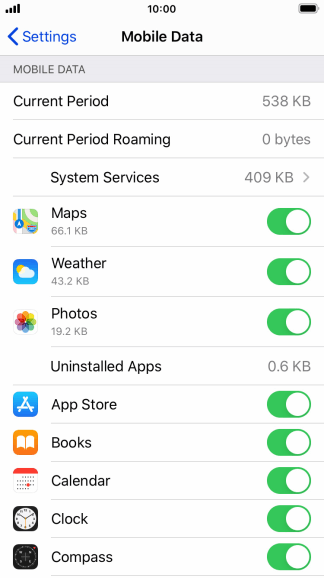
-
Track Battery Usage:
– Pay close attention to your battery usage patterns at all times. Battery drain rising significantly and without any reasonable explanation may point to remote access.
-
Monitor Data consumption:
– Regularly check your iPhone’s data consumption to look for any unusual patterns or irregularities that could indicate unauthorized access.
Preventing Possible Unauthorized Access
Preventing possible remote access to your iPhone requires proactive steps such as the following:
-
Keep Your iPhone Updated:
-To ensure that you receive the most recent security updates and fixes, make sure that the operating system on your iPhone is always kept up to date.
-
Make Use of Biometrics and Strong Passwords in case someone is accessing your iPhone:
– For increased security, create a strong alphanumeric passcode or make use of biometric authentication tools like Touch ID and Face ID.
Extra Security Measures
An extra layer of protection should be added to the security of your device by thinking about putting the following security procedures in place in addition to the basic protection:

-
Turn on two-factor authentication:
– Make sure you enable 2FA (two-factor authentication) for your Apple ID and any other important iPhone accounts for an additional layer of security.
-
Make use of Find My iPhone:
– Turn on Find My iPhone to track down your phone, remove its data if necessary, or enter lost mode.
Actions to Take if Someone is Accessing Your iPhone
If you are unable to suspect remote access, take quick action by doing the following:
-
Change Your Passwords if someone is accessing your iPhone:
– All credentials connected to a device that is connected to an iPhone, including your Apple ID password, need to be changed.
-
Get in touch with Apple Support:
– Lastly, get in touch with Apple Support for help in looking into and fixing the possible remote access by someone to your iPhone.
Conclusion
You can prevent unwanted access by taking caution and monitoring what your iPhone does. Your smartphone is safer when it has security features like two-factor authentication, strong passwords, and frequent upgrades. Simply be alert and often review your device’s settings and installed programs to guard against remote handling attacks. Safeguarding your iPhone involves not just preserving the device but also keeping track of the personal data it contains.
